Enterprise-level network devices on the secondary market conceal delicate information that hackers might utilize to breach business environments or to acquire client info.
Taking a look at numerous utilized corporate-grade routers, scientists discovered that the majority of them had actually been incorrectly cleaned throughout the decommissioning procedure and after that offered online.
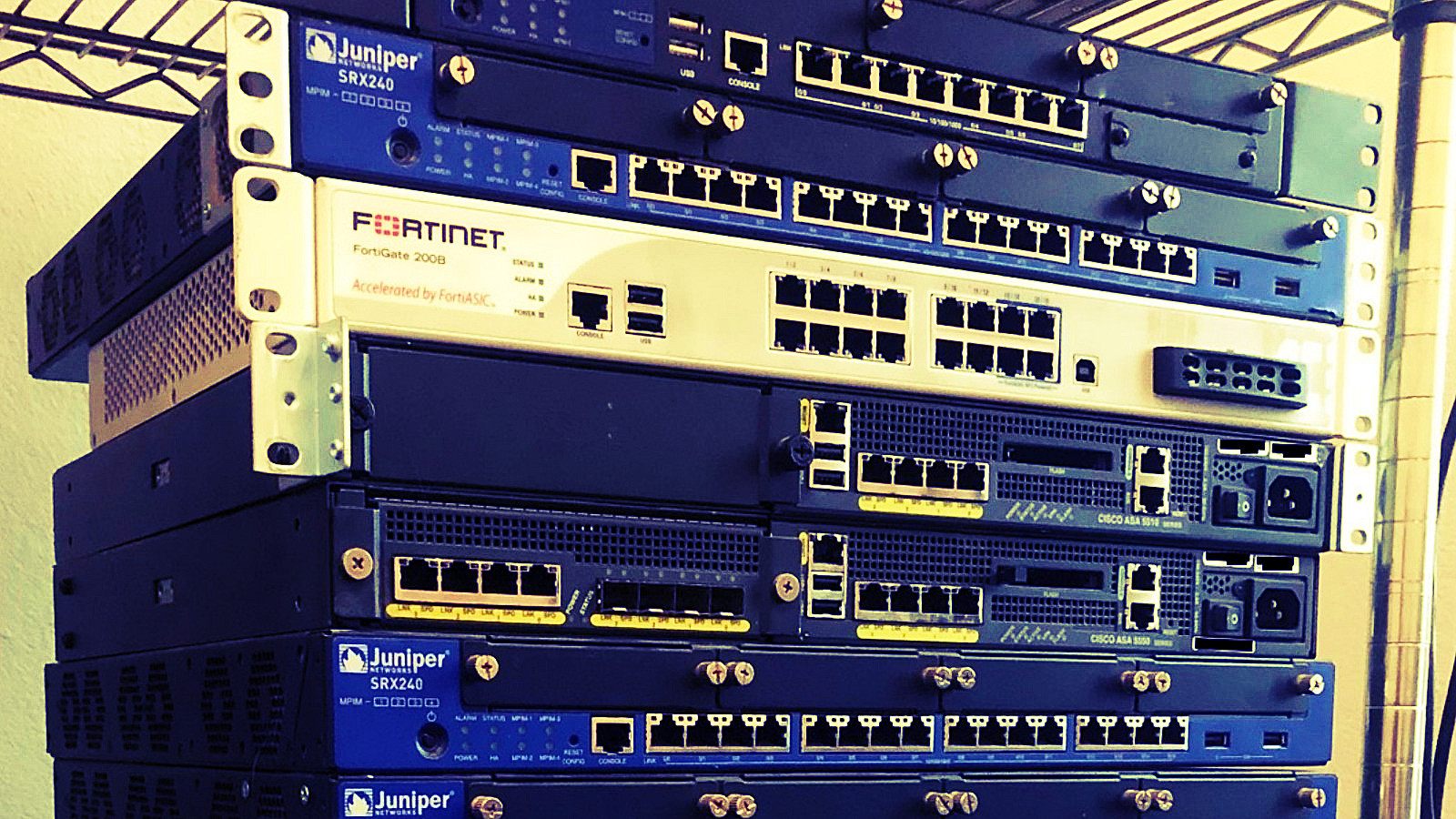
Core routers for sale
Scientists at cybersecurity business ESET bought 18 utilized core routers and discovered that the complete setup information might still be accessed on over half of those that worked appropriately.
Core routers are the foundation of a big network as they link all other network gadgets. They support several information interaction user interfaces and are developed to forward IP packages at the greatest speeds.
At First, the ESET research study group purchased a couple of utilized routers to establish a test environment and discovered they had actually not been appropriately cleaned and included network setup information along with info that assisted determine the previous owners.
The purchased devices consisted of 4 gadgets from Cisco (ASA 5500), 3 from Fortinet (Fortigate series), and 11 from Juniper Networks (SRX Series Provider Entrance).
In a report previously today, Cameron Camp and Tony Anscombe state that a person gadget was dead on arrival and gotten rid of from the tests and 2 of them were a mirror of each other and counted as one in the assessment results.
Of the staying 16 gadgets, just 5 were appropriately cleaned and simply 2 had actually been solidified, making a few of the information harder to gain access to.
For the majority of them, however, it was possible to access the total setup information, which is a chest of information about the owner, how they established the network, and the connections in between other systems.
With business network gadgets, the administrator requires to run a couple of commands to safely clean the setup and reset it. Without this, the routers can be booted into a healing mode that permits examining how it was established.
Tricks in the network
The scientists state that a few of the routers maintained client info, information that enabled third-party connections to the network, and even “qualifications for linking to other networks as a relied on celebration.”
Furthermore, 8 of the 9 routers that exposed the complete setup information likewise included router-to-router authentication secrets and hashes.
The list of business tricks encompassed finish maps of delicate applications hosted in your area or in the cloud. Some examples consist of Microsoft Exchange, Salesforce, SharePoint, Spiceworks, VMware Horizon, and SQL.
” Due to the granularity of the applications and the particular variations utilized in many cases, understood exploits might be released throughout the network geography that an enemy would currently have actually mapped” – ESET
Such comprehensive expert information are usually booked for “extremely credentialed workers” such as network administrators and their supervisors, the scientists discuss.
A foe with access to this kind of info might quickly create a prepare for an attack course that would take them deep inside the network undiscovered.
” With this level of information, impersonating network or internal hosts would be far easier for an enemy, specifically given that the gadgets frequently consist of VPN qualifications or other quickly broken authentication tokens” – ESET
Based upon the information discovered in the routers, numerous of them had actually remained in environments of handled IT service providers, who run the networks of big business.
One gadget even came from a handled security companies (MSSP) that dealt with networks for numerous customers in numerous sectors (e.g. education, financing, health care, production).
Following their findings, the scientists highlight the value of appropriately cleaning network gadgets prior to eliminating them. Business ought to have treatments in location for the protected damage and disposal of their digital devices.
The scientists likewise caution that utilizing a 3rd– celebration service for this activity might not constantly be a great concept. After informing the owner of a router of their findings, they found out that the business had actually utilized such a service. “That plainly didn’t go as prepared.”
The recommendations here is to follow the suggestions from the gadget maker to clean up the devices of possibly delicate information and bring it to a factory default state.